Disabling XML-RPC with the A2 Optimized for WordPress plugin
WordPress uses an XML-RPC interface to allow other websites or apps to interact with your site, but leaving it open poses a potential security risk. Learn how to disable XML-RPC in WordPress using the A2 Optimized for WordPress plugin.
XML-RPC is a Remote Procedure Call method that uses XML over HTTP. WordPress is configured to use an XML-RPC interface out of the box that enables other websites or apps to interact with your site. XML-RPC requires valid XML to be sent via HTTP posts, but leaving it enabled is a potential security risk because it can be used for SQL injection attacks, Server Side Forgery, and other malicious activities.
This article shows how to disable XML-RPC in WordPress using the A2 Optimized for WordPress plugin.
Disabling XML-RPC
To disable XML-RPC using the A2 Optimized for WordPress plugin, follow these steps:
-
Log in to your WordPress site as the administrator.
-
Under Dashboard, click A2 Optimized:
-
Click the Optimization tab:
-
In the left sidebar, click Security:
-
In the SECURITY section, at the bottom click More Optimizations:
-
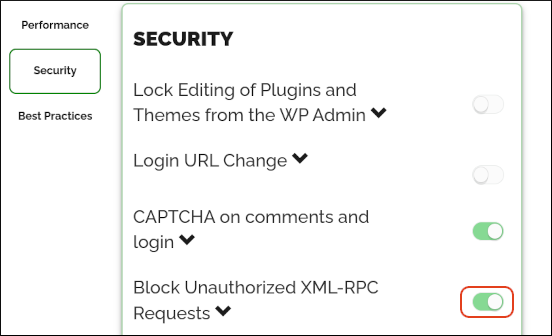
In the Block Unauthorized XML-RPC Requests row, click the slider to enable or disable blocking:
More information
For more information about the XML-RPC service for WordPress, please visit https://codex.wordpress.org/XML-RPC_Support.
Related articles
Updated 16 days ago
